ConsoleWorks acts in a multi-dimensional fashion by monitoring not only the applications but also the servers, virtual machines, networks, and storage devices that run them. It provides managers and administrators with an end-to-end management solution that controls system access, monitors and manages all log files, and watches for specific events that may occur across the Enterprise.
And it does all of this in real-time and in all machine states – power on, single user, maintenance, production, and failure modes. This persistent connection also locks down the “back door” entrances that are overlooked by similar, agent-based solutions.
The end-to-end view provided by ConsoleWorks helps administrators understand why something went wrong and quickly determine and implement the resolution. During that process, ConsoleWorks captures the exact steps used by an experienced administrator to remediate an issue and stores it in the knowledge base for future reference.
ConsoleWorks achieves end-to-end monitoring and management with the following capabilities:
- Secure Access Management
- Event Correlation
- Log File Aggregation
- Keystroke Logging & Best Practices
- Proof of Compliance
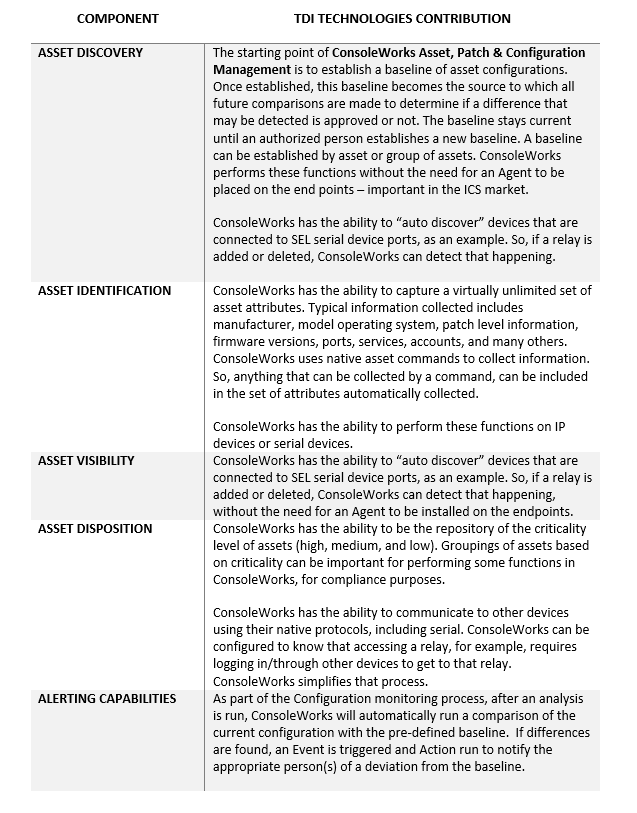
ConsoleWorks automates the collection, comparison, alert/notification and auditing of any changes to configuration baselines, eliminating the majority of human errors and minimizing the impact of intentional or unintentional erroneous activity.
ConsoleWorks has the ability to speak multiple protocols (including serial), gaining access to and then collecting the inventory is a fundamental capability of the product. ConsoleWorks does this without adding an Agent to the endpoint, which is a requirement in the ICS environment since many of these devices are purpose-built and cannot have other vendor software installed on it.
ConsoleWorks can be configured to monitor many items including:
- Functional settings that determine how the asset operates
- Versions of software currently installed including BIOS, firmware, operating system, applications, etc.
- Patches, including security patches that are installed
- Ports that are active and how they are configured
- Services that are enabled
- Accounts
- Configuration Files