As part of ConsoleWorks’ robust Secure Remote Access capabilities, the Just-in-Time Request Access feature greatly enhances security by enabling specific control over when users, including employees, contractors and vendors, are granted access to critical devices. For example, the owner of a group of devices running a critical application, such as email, or a plant manager in a specific location, can control when access is granted, effectively minimizing the attack surface.
The Request Access feature is highly configurable and can be enabled or disabled on a device-by-device basis. If enabled, the device icon appears as muted, indicating that it can only be accessed by request. The requestor can select one or multiple devices requiring access and provide a timeframe for immediate or future access. A specific duration can be requested or a default can be defined.
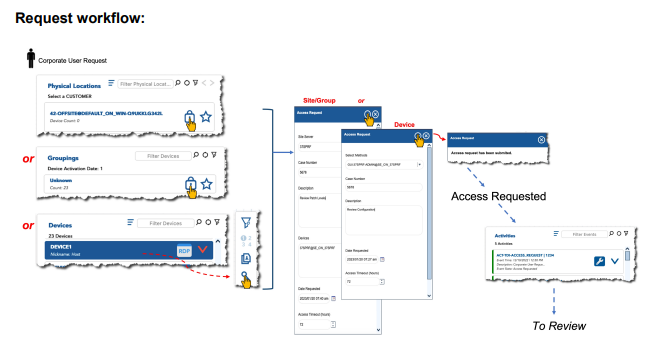
After the request is submitted, ConsoleWorks notifies the appropriate approver, who then approves or denies access. Throughout the process, the requestor is provided with status indicators of where the approval is in the flow.
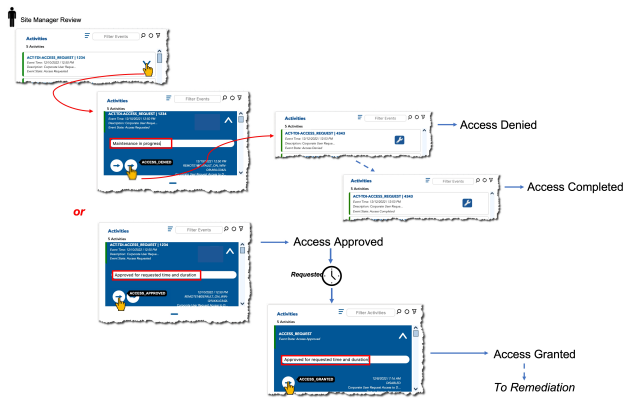
By enabling access by request only, ConsoleWorks helps organizations reduce the risk of unauthorized access to critical devices, minimizes insider threats and further strengthens compliance requirements with audit reports with relevant information, enhancing visibility and oversight.
File Download
ConsoleWorks is designed to empower users to perform their jobs securely and one area where it excels is file transfer. Unlike other Secure Remote Access solutions, ConsoleWorks offers robust features to safeguard critical infrastructure against malware and viruses.
The first layer of protection inherent to ConsoleWorks is a protocol break between the user’s laptop and the device. This provides a secure barrier between the user’s device and the infrastructure, preventing any malicious software from penetrating the network accidentally. Optionally, ConsoleWorks integrates with file scanning technology to ensure that files transferred to a device are free from malware and viruses.
To transfer files from a user’s laptop to a device, ConsoleWorks employs a three-step process. First, the file is moved from the user’s laptop to ConsoleWorks. Second (if desired) if a file scanning solution like the one available from ODIX is used, the file is automatically placed in a “Dirty” folder. If a file appears in that folder, ODIX will scan it and clean it. Once the file has been scanned and found to be free of malware and viruses, it is moved to a “Clean” folder on ConsoleWorks. Finally, the file is then transferred to the destination device, which can be either local or on the network.
With its advanced security features and user-friendly interface, ConsoleWorks provides a reliable and secure solution for file transfer. To see ConsoleWorks in action or how it can help for your use cases, talk to us here.
