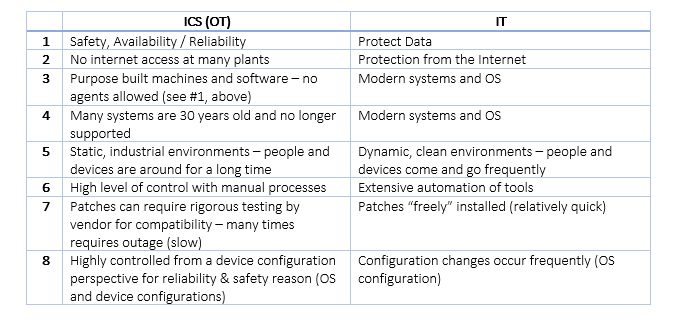
Having a configuration port cybersecurity strategy for critical and non-critical cyber assets is important but often overlooked in the overall cybersecurity strategy. Virtually all electronic devices with communication capability have configuration ports, and these ports present an extremely high set of privileges that can be used to change almost anything on the target device. Failing to secure these ports results in a significant security risk.
Unfortunately, configuration port security is a commonly misunderstood area of cybersecurity. Security guidelines often provide broad statements such as “all ports should be either secured or disabled,” which obviously includes configuration ports. However, configuration ports should not be disabled as they are the default emergency access point for every IT and OT asset. Instead, they must be effectively secured.
View Configuration Monitoring Datasheet
View Configuration Monitoring NERC CIP 010 Datasheet

 TDi is lead sponsor at the 2018
TDi is lead sponsor at the 2018