Compromised passwords are one of your biggest liabilities. For many companies with low password management maturity, a compromised password can have devastating outcomes. Our multi-factor authentication best practices are helping you increase security against your password vulnerabilities.
It’s important to attach more security to your credentials. It’s not uncommon for password sharing and using the same password across devices to take place, especially when there is a large amount of devices involved. While it’s important you adhere to password best practices in general, following MFA best practices will help you secure against common vulnerabilities and challenges.
What is Multi-factor Authentication
Passwords today are an easy entry point for bad actors. Multi-factor authentication is a method of authentication that requires more than just a user’s password to authenticate the user. It is an enhanced version of two-factor authentication, which also requires more than just the user’s password to complete the authentication.
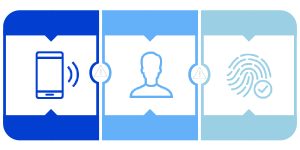
Multifactor authentication will include at least two authentication methods, though it can include more. These authentications are focused on three areas: something you know, something you have and something you are.
Something you know is typically the user ID and password. This is then layered in with something you have, generally a security token that is generated that only the user will have. With the something you are method of authentication, this will also authenticate based on biometric data of the user.
Additionally, MFA might require additional contextual factors, such as location or time to finalize authentication.
What Are the Benefits of Multifactor Authentication
MFA makes you a harder target. It’s part of CISA’s Shields Up and is used in Zero Trust architectures as a security measure. NIST as well recommends MFA whenever possible. As passwords are often targeted by attackers, you want to make sure that you are doing your best to secure them.
By implementing more authentication requirements, you are making yourself a more difficult target. While a password may end up compromised, the additional authentication factors act as an additional wall of defense against the threat gaining entry through the compromised account.
Multi-factor Authentication Benefits
- Improve the security of your credentials
- Support more advanced cybersecurity measures like Zero Trust
- Flexibility to choose various methods of authenticating a user
- Meet compliance or regulatory needs
Multi-factor Authentication Best Practices
Implement Multi-factor Authentication Across the Business
Any unsecured password is a vulnerability. The last thing you want to do is secure part of your house by locking the doors, but still leave the windows open. This should be one of your top multi-factor authentication best practices that you follow. When you are ready to secure your passwords and business with this implementation, be sure to go all the way and make sure every user is authenticating this way.
Leverage the “Multi-factor” Functionality
Determine what authentication factors are best for you and the business. As we mentioned above, there are various methods a user can take to authenticate their selves and you can choose two or more, depending on needs. You want to choose the best form of authenticating that doesn’t introduce friction into the process and also keeps you as secure as possible. Be sure to review your options for authentication and then settle on the options that make the most sense.
Combine Your MFA With Other Security Tools
While following these MFA best practices will help you become more secure, you still have many additional tools and approaches you can leverage to further enhance your security. You should be considering other things like secure remote access that offers least-privileged access at the right time, only when it is needed. While implementing your MFA, it is a good time to start considering these additional approaches as well.
Make Implementation Frictionless
ConsoleWorks already supports multi-factor authentication in addition to enabling other critical Zero Trust traits and features. When considering your implementation, evaluate your roadmap and see what is on the horizon. You don’t want to have technology silos, so make sure you’re picking a technology that can do more for you. This is why our security platform helps with secure remote access, logging and monitoring, baseline configuration monitoring and password management. You are able to plan your security within an ecosystem that you grow into, not out of.
Go Beyond MFA Best Practices to Enhance Security with Zero Trust
While these multifactor authentication best practices will enhance your security and make it harder for a bad actor to gain entry, it is not without its vulnerabilities. For a true network defense that is ready to defend against today’s threats, we recommend going beyond and attaining a Zero Trust defense.
You can see our Zero Trust maturity model, which shows you where you are in your journey to achieving this defense. If you have any questions about where you are now or where you want to go with your cybersecurity, we are right here to talk with you.