Available Q2 2018
The new, Automated Patch Analysis Process from ConsoleWorks will be applicable to various IT/OT patching processes including, PCI-DSS, NIST 800-53, HIPAA, NERC CIP and others.
Automated Patch Analysis Process Use Case: NERC CIP-007-6/R2
NERC CIP-007-6 / R2 requires a patch management process for tracking, evaluating, and installing cybersecurity patches for applicable Cyber Assets, including device drivers. Many utilities see this is a grueling task, requiring many, many man-hours to meet the “every 35-day analysis” required by NERC CIP.
Many utilities are in various stages of implementation of an effective solution with most relying on a manual update of a database, or spreadsheet, that contains the latest patch versions entered for each asset. Traditionally, the asset information has been manually gathered and manually entered since these approaches are disconnected from the assets. These and other manual approaches not only result in inconsistencies and errors, but are enormously labor intensive.
The ConsoleWorks Automated Patch Analysis solution greatly simplifies the process of gathering the information required for patching IT and OT devices – beyond the HMI.
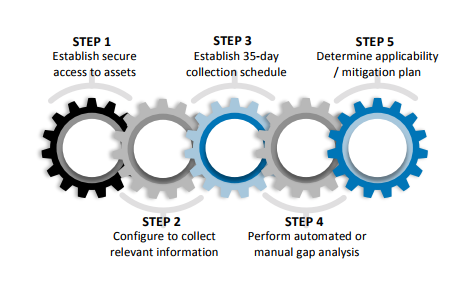
For meeting NERC CIP compliance, ConsoleWorks establishes a secure access to access all devices and then is configured via a schedule to perform the patch analysis every 35 days, keeping a log, for audit purposes, of when the analysis was run. Once the current patch state is gathered by ConsoleWorks, ConsoleWorks can integrate with industry or custom solutions to assist in automating the patch gap analysis. In these cases, ConsoleWorks sanitizes, anonymizes, and encrypts the data before initiating the secure transfer of the collected device information.
After the initial collection is sent, ConsoleWorks can be configured to continually monitor for the patch gap analysis results. When available, ConsoleWorks automatically downloads and processes the results, using ConsoleWorks Events as an indication to the user when patches are available. Event Severities further indicate whether an available patch is a security patch.
Finally, ConsoleWorks produces dashboard report views to organize and communicate the current patch state. ConsoleWorks presents a summary report containing information on patch gaps that may exist for each asset, including links to any available patch for downloading directly from the vendor site.
At this point, a utility will evaluate the available security patch for applicability and make the decision to install the patch or initiate a mitigation plan. ConsoleWorks’ integration with workflow management solutions enables utilities to further automate the patching and mitigation processes as required by NERC.
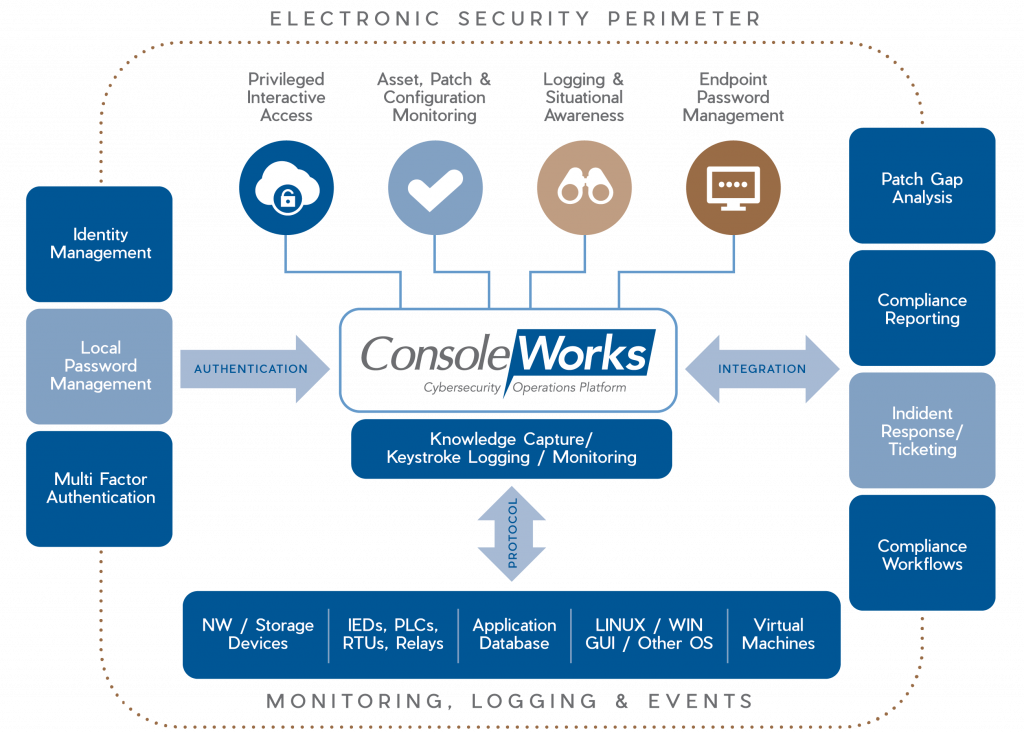
The patch analysis features will be available in ConsoleWorks in Q2, 2018, and are part of a larger cybersecurity and operations platform solution addressing IT/OT patching processes for PCI-DSS, NIST-800-53, HIPAA, NERC CIP V6 ( CIP-005, CIP-007, CIP-010, and CIP-013) requirements for Secure Remote Access, Asset and Configuration Monitoring, Endpoint Password Management, Logging and Situational Awareness and Supply Chain.



