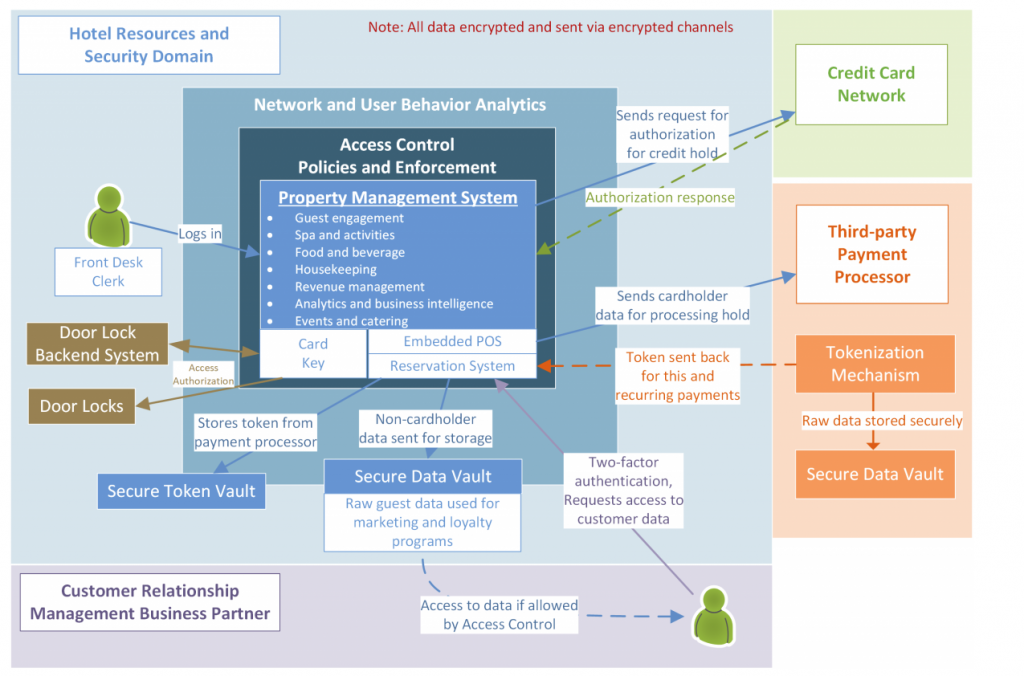
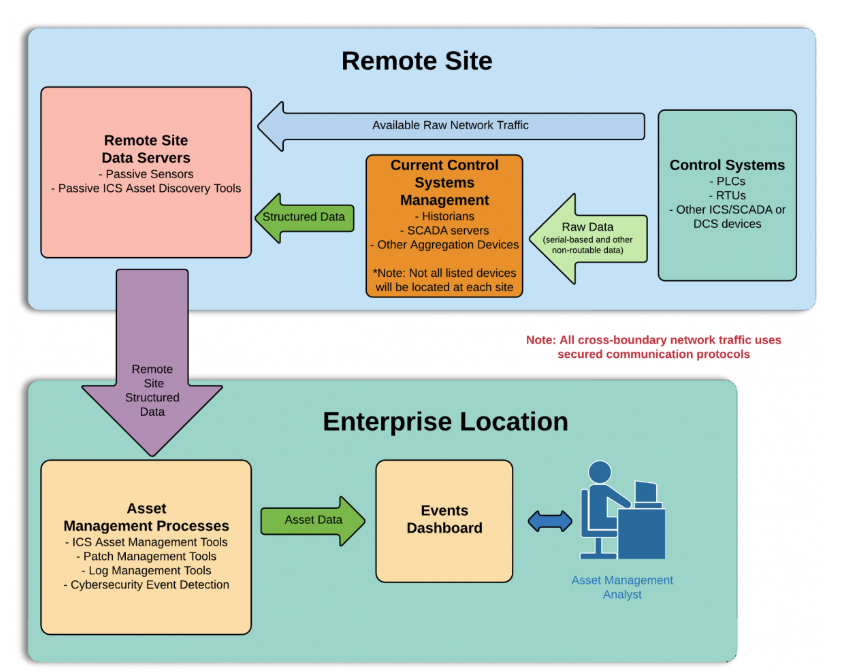
Anterix, BlackRidge Technology, Cisco, Radiflow, Spherical Analytics, Sumo Logic, TDi Technologies, and Xage Security have joined the National Cybersecurity Center of Excellence (NCCoE) as technology collaborators in the Securing the Industrial Internet of Things (IIoT): Cybersecurity for Distributed Energy Resources Project.*
In response to a call in the Federal Register, these companies submitted capabilities that aligned with desired solution characteristics listed in the project description and were invited to collaborate with the NCCOE. By signing a cooperative research and development agreement (see example), they will collaborate in a newly established consortium and contribute products and expertise to create a standards-based reference design for IIoT cybersecurity focused on data integrity.
This collaboration will result in a publicly available National Institute of Standards and Technology (NIST) Cybersecurity Practice Guide (Special Publication 1800 series), which will document the reference design for securing IIoT in commercial- and/or utility-scale distributed energy resource (DER) environments and will include an example solution that uses existing, commercially available cybersecurity products.
TDi is working with the National Institute of Standards and Technology’s (NIST’s) National Cybersecurity Center of Excellence (NCCoE) in the Securing the Industrial Internet of Things (IIoT) Use Case to develop practical, interoperable cybersecurity approaches that address the real-world needs of distributed energy resource environments. By accelerating dissemination and use of these integrated tools and technologies for protecting IIoT in and among distributed energy resources, the NCCoE will enhance trust in U.S. information technology (IT) and operational technology (OT) communications, data, and storage systems; reduce risk for companies and individuals using IT/OT systems; and encourage development of innovative, job-creating cybersecurity products and services. NIST does not evaluate commercial products under this consortium and does not endorse any product or service used. Additional information on this consortium can be found at https://www.nccoe.nist.gov/projects/use-cases/energy-sector/asset-management.
The U.S. Power Grid is Moving Toward a Future Full of DERs
Use of DERs—such as wind and solar photovoltaics—is growing and transforming the traditional power grid. As the use of DERs expands, the distribution network is changing from a single-source radial network to a multisource grid of devices and systems. Proper management of these devices and their power flows is heavily dependent on digital communication and control across public communication networks. DER integration—driven by IIoT devices, data flow, and information management—poses a widening attack surface and growing cybersecurity challenge for the energy sector.
This NCCoE project will focus on helping energy companies secure IIoT information exchanges of DERs in their operating environments. The solution will use security controls that map to the NIST Cybersecurity Framework and industry standards and best practices. The project will result in a freely available NIST cybersecurity practice guide and document an approach for improving the overall security of IIoT in a DER environment. The project will address the following areas of interest:
- the information exchanges between and among DER systems and distribution facilities/entities and the cybersecurity considerations involved in these interactions
- the processes and cybersecurity technologies needed for trusted device identification and communication with other devices
- the ability to provide malware prevention, detection, and mitigation in operating environments where information exchanges are occurring
- the mechanisms that can be used for protecting both system and data transmission components
- data-driven cybersecurity analytics to help owners and operators securely perform necessary tasks
How to Participate
Interested parties are encouraged to engage with us through our project web page.
If you have additional comments or questions or would like to join the Community of Interest helping to guide this project and providing feedback, please email us at energy_nccoe@nist.gov.
Key URLs
Below are some key uniform resource locators (URLs) that link to the practice guide and the comment form.
- Project page URL: https://www.nccoe.nist.gov/projects/use-cases/energy-sector/iiot
- Project fact sheet: https://www.nccoe.nist.gov/sites/default/files/library/fact-sheets/es-iiot-fact-sheet.pdf
Frequently Asked Questions
What Is IIoT?
Industrial Internet of Things (IIoT) can be defined in many ways. The National Cybersecurity Center of Excellence (NCCoE) does not seek to authoritatively define IIoT but rather to provide examples of generally accepted IIoT applications in the real world and the commensurate cybersecurity challenges that arise. That said, there are several characteristics of IIoT, such as:
- IIoT is similar in concept to a collection of Internet of Things devices that are used for industrial purposes.
- An IIoT device can provide computation and communication combined with one or more of the following functions: sensing, actuation, storage.
- An IIoT device may perform its function(s) without user interaction.
In this project, the IIoT comprises interconnected sensors, data transfer and communications systems, instruments, and other commercial off-the-shelf devices networked together for an industrial purpose—providing electricity to the grid.
What Are the Challenges for DER Infrastructure?
In the energy sector, distributed energy resources (DERs), such as solar photovoltaics and wind turbines, introduce information exchanges between a utility’s distribution control system and the DERs to manage the flow of energy in the distribution grid. These information exchanges often employ IIoT technologies that may lack communications security. Additionally, the operating characteristics of DERs are dynamic and significantly different from those of traditional power generation capabilities, and the DERs may not be owned by or configurable by the distribution utility. Timely management of DER capabilities often requires a higher degree of automation. Introduction of additional automation into DER management and control systems can also introduce cybersecurity risks. Managing the automation, the increased need for information exchanges, and the cybersecurity associated with these presents significant challenges.
What Do You Hope to Demonstrate in This Project?
This project explores several scenarios in which information exchanges among commercial- and utility-scale DERs and electric distribution grid operations can be protected from certain cybersecurity compromises. The following cybersecurity capabilities will be demonstrated:
- analysis and visualization processes to monitor data, identify anomalies, and alert operators
- behavioral monitoring to detect deviations from operational norms
- communications integrity to ensure that information is not modified in transit
- authentication and access control to ensure that only known, authorized systems can exchange information
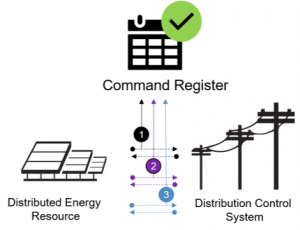
- command register that maintains an independent, immutable record of information exchanges between distribution and DER operators
- malware detection to monitor information exchanges and processing to identify potential malware infections
How Was Your Company Selected to Collaborate in This Project?
We responded to a Federal Register notice that invited cybersecurity vendors and other interested collaborators to participate in the project. The NCCoE then selected companies that submitted a completed Letter of Interest on a first-come, first-served basis within each category of components or characteristics/capabilities listed in the Federal Register notice up to the number of participants in each category necessary to carry out the project build.
Will NIST Be Developing Standards for DER Cybersecurity in This Project?
No. NCCoE projects do not create standards; rather, they demonstrate how to apply National Institute of Standards and Technology (NIST) and industry standards to help solve specific cybersecurity challenges.
What Is a Command Register?
We refer to a command register as the means to capture the sequence of events related to DER management across all DERs connected to, monitored, and controlled by a distribution control system. Its purpose is to provide an immutable record of transactions/communications among a distribution control system and the control systems managing the DER, verify the integrity of information exchanges, and provide a comprehensive audit trail of information exchanges.
About the National Cybersecurity Center of Excellence
The NCCoE, a part of NIST, is a collaborative hub where industry organizations, government agencies, and academic institutions work together to address businesses’ most pressing cybersecurity issues. This public-private partnership enables creation of practical cybersecurity solutions for specific industries, as well as for broad, cross-sector technology challenges. Through consortia under CRADAs, including technology partners—from Fortune 50 market leaders to smaller companies specializing in information technology and operational technology security—the NCCoE applies standards and best practices to develop modular, easily adaptable example cybersecurity solutions by using commercially available technology. The NCCoE documents these example solutions in the NIST Special Publication 1800 series, which maps capabilities to the NIST Cybersecurity Framework and details the steps needed for another entity to re-create the example solution. The NCCoE was established in 2012 by NIST in partnership with the State of Maryland and Montgomery County, Maryland. Information is available at https://www.nccoe.nist.gov.
*Certain commercial entities, equipment, products, or materials may be identified to describe an experimental procedure or concept adequately. Such identification is not intended to imply recommendation or endorsement by NIST or NCCoE, nor is it intended to imply that the entities, equipment, products, or materials are necessarily the best available for the purpose.